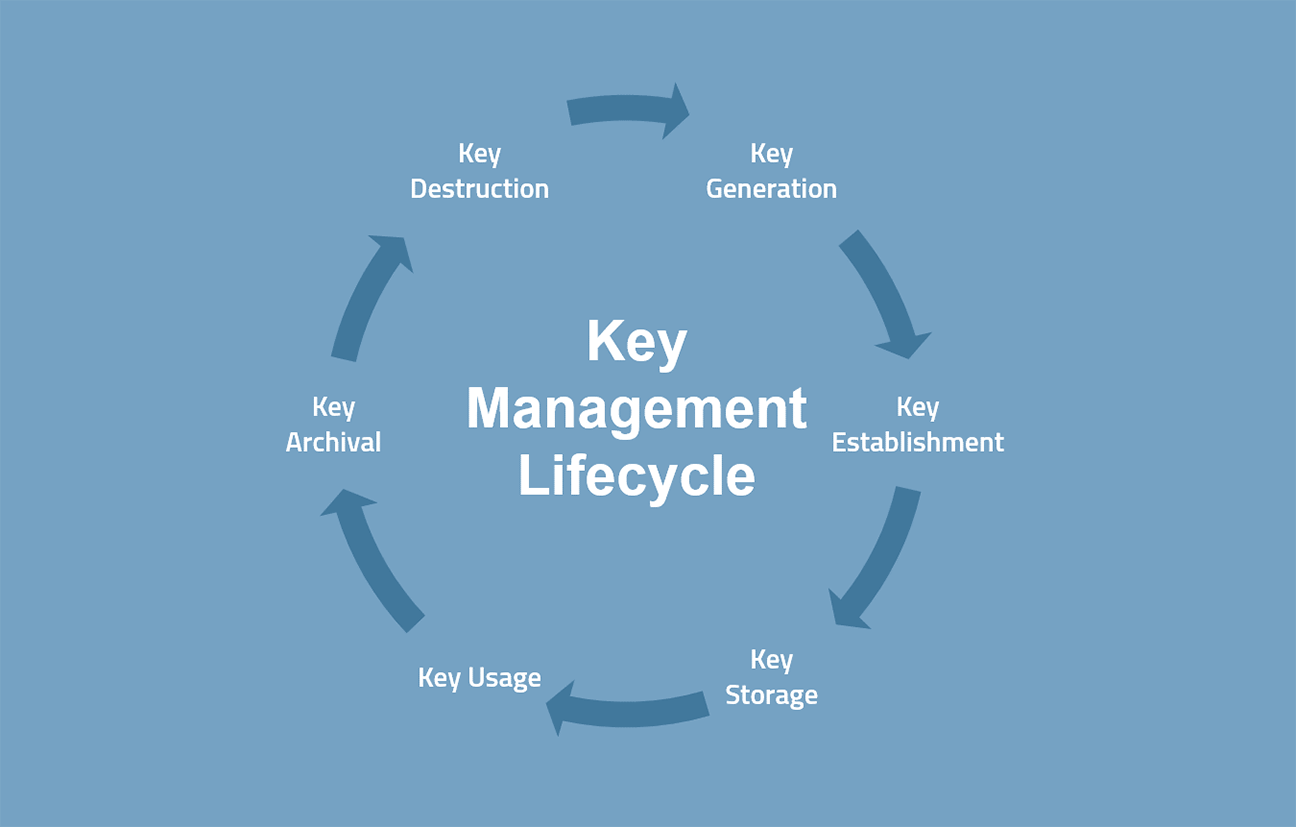
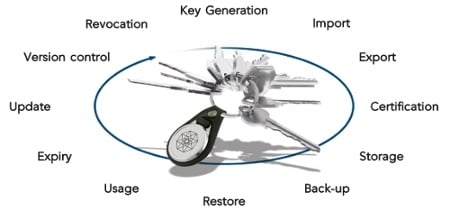
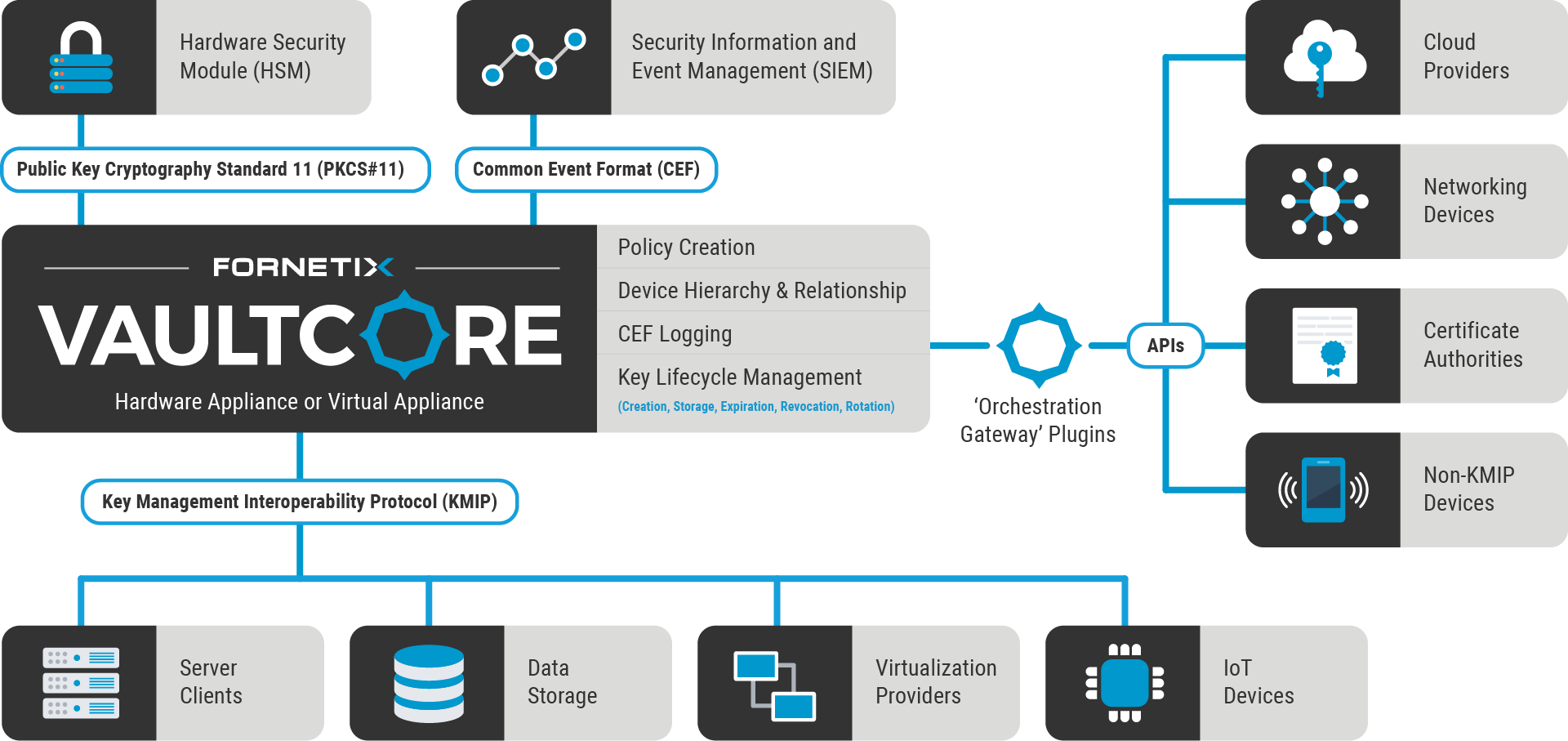
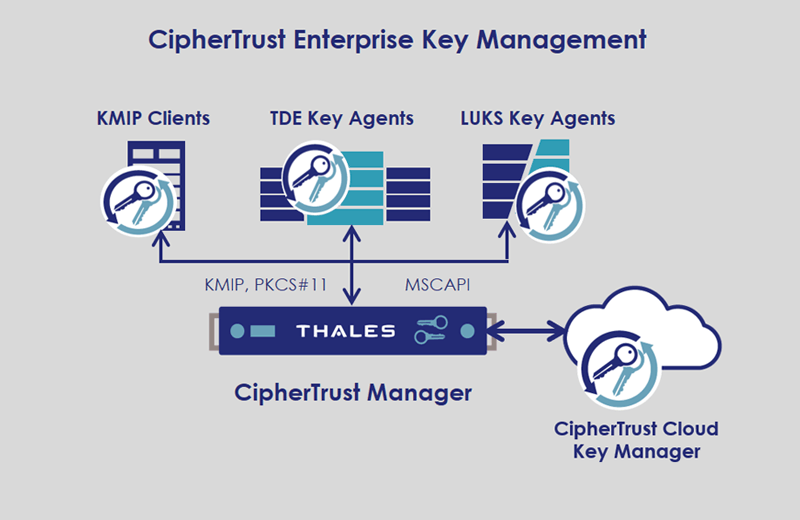
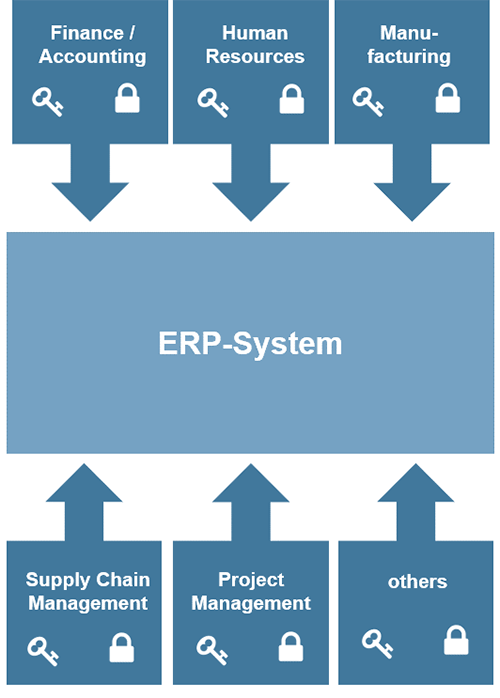
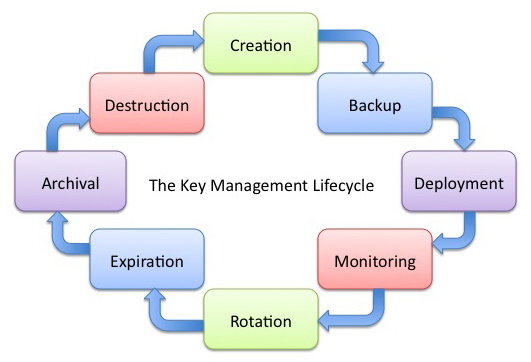
Benefits of External Key Management System Over the Internal and How they Could Help Securing PostgreSQL - Highgo Software Inc.

Demystifying KMS keys operations, bring your own key (BYOK), custom key store, and ciphertext portability | AWS Security Blog

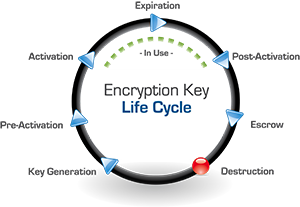
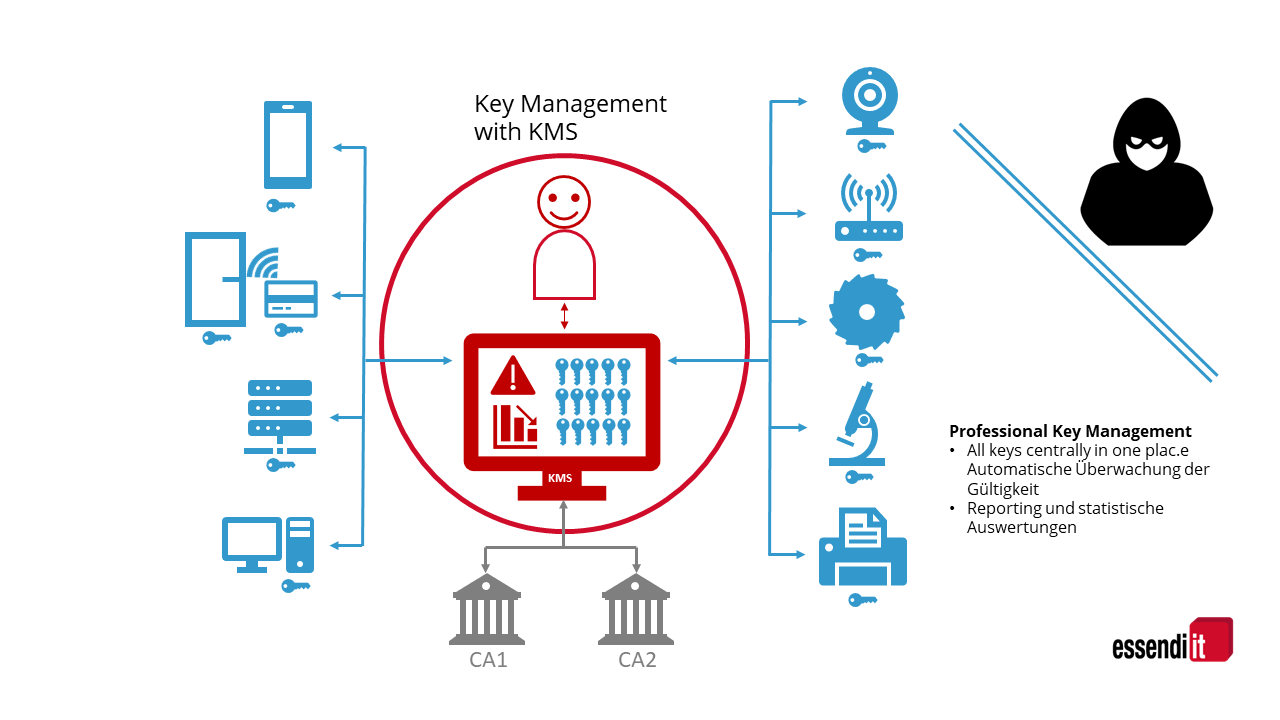

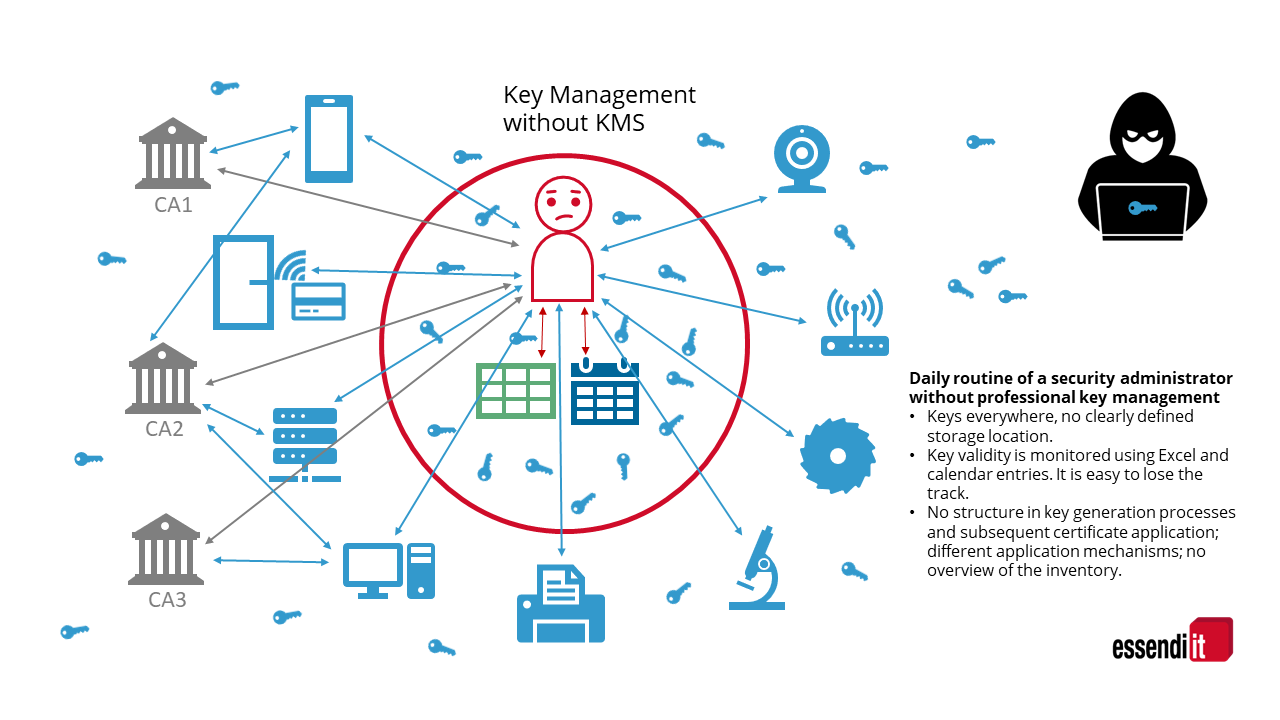

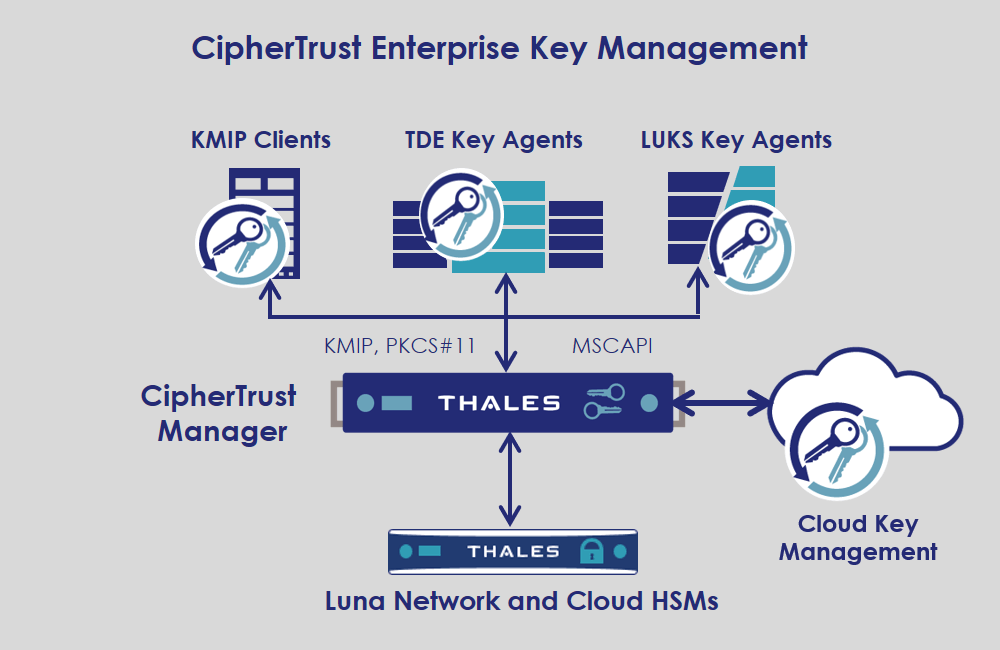
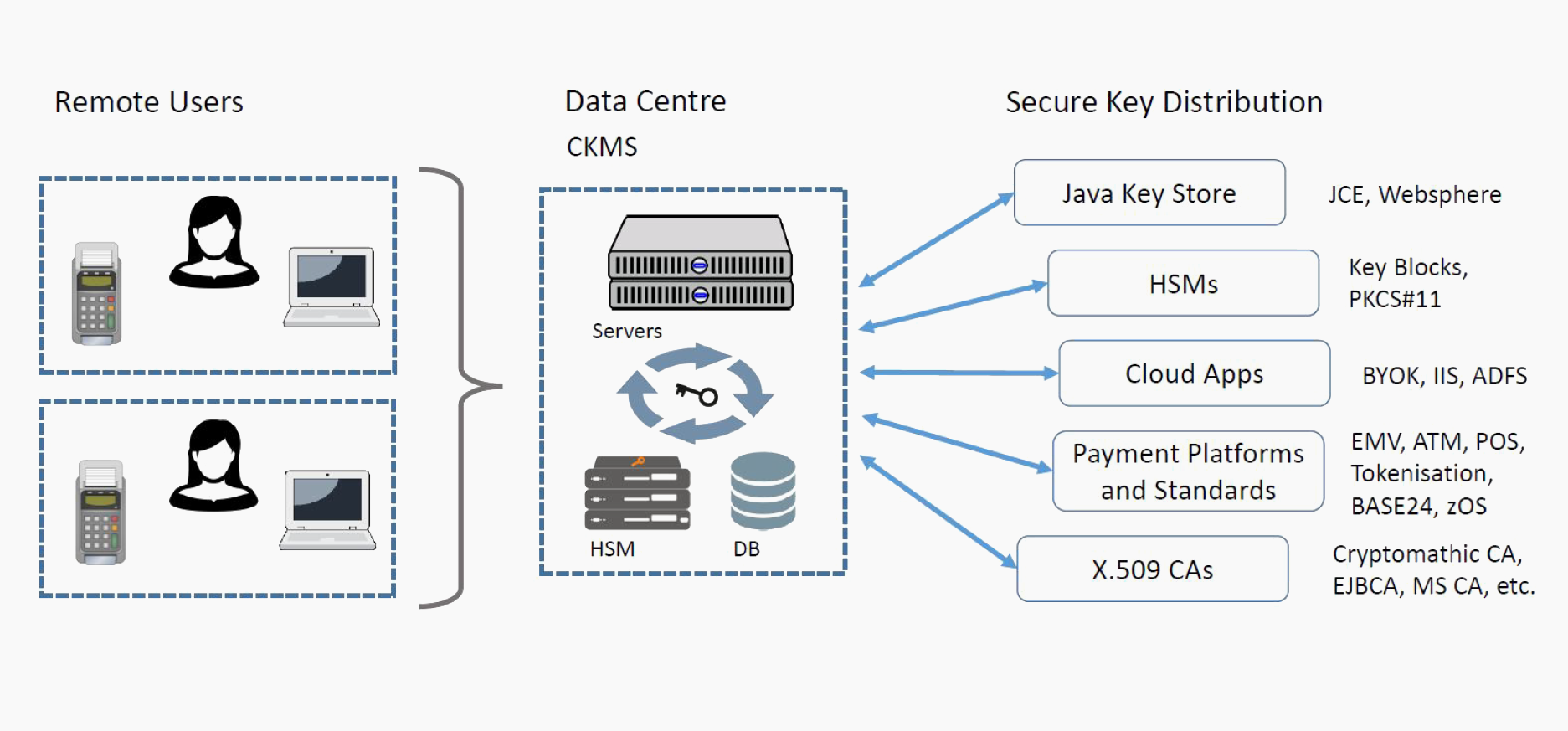
![PDF] A Framework for Designing Cryptographic Key Management Systems | Semantic Scholar PDF] A Framework for Designing Cryptographic Key Management Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/70d0c118e8b305c8d2d05c6eb8e6d9dea6a2a138/16-Figure1-1.png)